Part 2 — Blockchain 101
In the previous part, we had a broad view of blockchain technology and how it is structured.
We identified the key, core elements that make the blockchain such an interesting technology and so disruptive for so many fields, for its potential use cases and transparency.
One, and perhaps the most important core component is the Cryptography (derived from the Greek word kryptos, which means hidden) and is nothing less than the science of sending messages back and forth from one party to another in the presence of ADVERSARIES or BAD ACTORS participants who wish to CORRUPT the content of the message.
There are five primary functions of cryptography:
. Privacy/confidentiality: Ensuring that no one can read the message except the intended receiver;
. Authentication: The process of proving one’s identity;
. Integrity: Assuring the receiver that the received message has not been altered in any way from the original;
. Non-repudiation: A mechanism to prove that the sender really sent this message;
. Key exchange: The method by which crypto keys are shared between sender and receiver.
It is closely associated with encryption, which is the act of scrambling ordinary text into what’s known as ciphertext and then back again upon arrival.
Cryptography is therefore, a 2-way function with 4 key components:
- the SECRET = the data which we are trying to protect;
- the KEY = a piece of data used to encrypt and decrypt the secret;
- the FUNCTION = an algorithmic function (called “hash”) used to encrypt the message;
- the CIPHER = the encrypted secret data (aka the output of the function).


Ancient Egyptians were known to use these methods in complex hieroglyphics, and Roman Emperor Julius Caesar is credited with using one of the first modern ciphers.
In today’s computer-centric world, cryptography is an indispensable tool for protecting information in computer systems, and the simplest method of cryptography uses the symmetric or “secret key” system.
Here, data is encrypted using a secret key, and then both the encoded message and secret key are sent to the recipient for decryption.
There is a problem though…
If the message is intercepted, a third party has everything they need to decrypt and read the message.
To address this issue, cryptologists devised the asymmetric or “public key” system. In this case, every user has two keys: one public and one private. Senders request the public key of their intended recipient, encrypt the message and send it along. When the message arrives, only the recipient’s private key will decode it — meaning theft is of no use without the corresponding private key.

How various Cryptographic Algorithms Works?
Let’s have a quick glance at the various algorithms available:
PUBLIC KEY CRYPTOGRAPHY: pair of public and private keys used for encryption and digital signatures;
Therefore will be required a set of :
_ PUBLIC KEY = used to verify that the message did actually come from the source it says it did;
_ PRIVATE KEY = used to sign the transaction on the blockchain.

ZERO-KNOWLEDGE PROOFS: prove knowledge of a secret without revealing it (increasing the privacy of the users):
We can explain it in bare terms using the “CAVE DOOR analogy”: there is one circular cave with only one entrance or exit.
At the back of the cave, there is a door that can be unlocked using a secret code entered onto a keypad.
If I want to prove to you that I can unlock the door without revealing the code, all I need is to show you that I can walk into one end of the cave and come out from the other end.
HASH FUNCTIONS: ONE-WAY pseudo-random mathematical functions and MERKLE TREES ( is a hash-based data structure that is a generalization of the hash list):

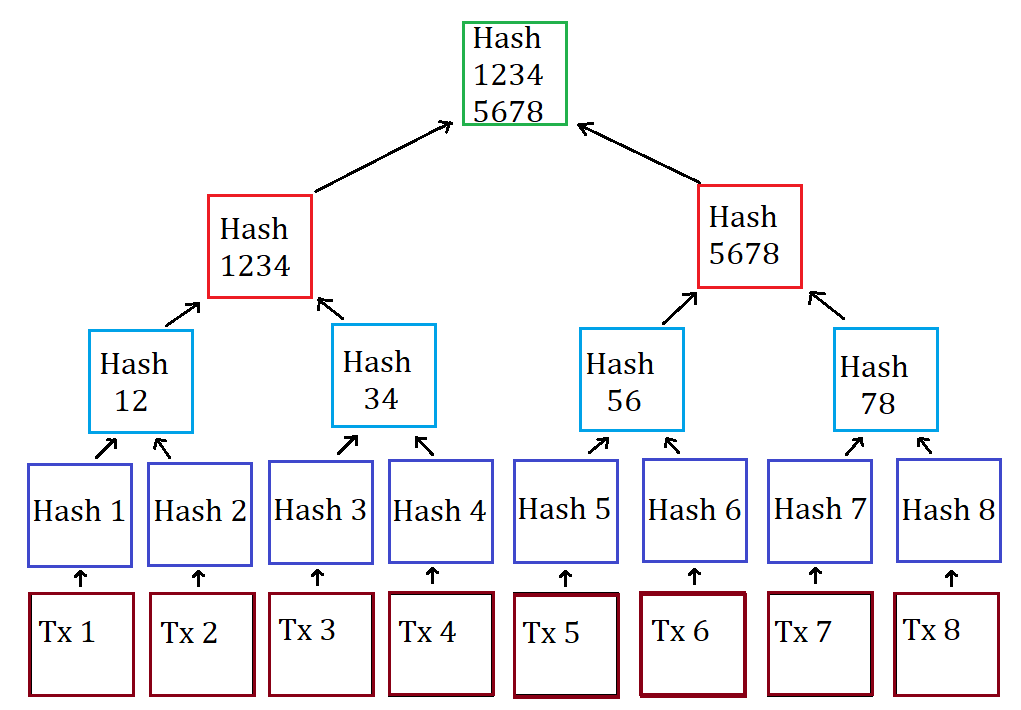
- easy to calculate the hash BUT HARD to determine the HASH INPUT from the OUTPUT (keep trying inputs to produce the desired output, but every incorrect input will produce a different hash);
- inputs that differ by a SINGLE BIT will produce a different OUTPUT that differs by half of their bits (on average), and it’s defined as “Concept of HILL CLIMBING”:
- — impracticable and not easy to do, to find 2 inputs that produce the same output when hashed;
- — one of the core uses of hash is chaining blocks together.
Here below is an interesting interactive example for you to try of chained blocks of information run along with the Blockchain.
You can see the hash output of every block and how it can dramatically differ from the previous by changing a single bit of information:
Cryptography is a fascinating area with active research to this day with abundant amounts of information for inquisitive minds.
Considering our modern-day computer/digital driven era, vast amounts of personal information are managed online and stored in the cloud or on servers with an ongoing connection to the web.
It’s nearly impossible to do business of any kind without our personal data ending up in an organization’s networked computer system, which is why it’s important to know how to help keep that data private.
Cryptography and encryption play an essential role in keeping our data secure, allowing transparency and incorruptibility of such data.

