Bridges are protocols connecting two blockchains, allowing them to interact with each other. A bridge allows for example to transfer USDC stablecoins from the Ethereum blockchain to the Solana blockchain, with ease. But what exactly is a bridge and how does it work? Focus on a fundamental type of protocol for cryptocurrencies and decentralized finance (DeFi).
1 What is a bridge between blockchains?
1.1 How does a bridge work?
2 Why is a bridge useful?
3 Why are bridges so vulnerable?
3.1 A certain pessimism among industry players
4 Our opinion on bridges
What is a bridge between blockchains?
Bridges arise from a need for communication and mobility of assets between blockchains. These are protocols that connect blockchains together .
With the advent of layer 1 blockchains, we could see the outlines of a multi-chain future for the cryptocurrency industry instead of the idea that a single blockchain would sit at the top and be used by all.
This proliferation of layer 1 blockchains and second layer (layer 2) solutions, along with a growing number of cross-chain decentralized applications (Dapps) that form the Web3 , has led to the need for an infrastructure to connect them .
Indeed, by default, the majority of blockchains exist in isolated environments , having their own rules, governance mechanisms, native assets and data that are incompatible with other blockchains .
There is therefore no native way for them to exchange and communicate with each other, which can limit activity and innovation due to the lack of connectivity and interoperability with other ecosystems.
Bridges thus offer a way to connect these isolated blockchains. They establish a gateway between networks through which smart contracts, data, tokens and various information can be transferred from one chain to another.
Concretely, if we have an ETH on the Ethereum network and we want to use it on the Near network, it is impossible natively. It is therefore necessary to use bridges to connect the two networks.

Figure 1: Illustration of Near Protocol’s Rainbow Bridge that links Ethereum and Near blockchains
There are several types of bridges since there is not only one way for blockchains to communicate with each other and each of these bridges has its own advantages and disadvantages.
How does a bridge work?
Bridges make it possible to open a one -way or two-way communication channel between different blockchains. In order for this to work and for them to be able to trust each other, off-chain actors have the task of verifying communications.
So, based on this key verification method for establishing trust during communications, we can basically classify bridges into two categories:
- Centralized bridges : rely on a third party to validate transactions and especially to keep “bridged” assets . Users then have no choice but to trust this intermediary to use it and manage their funds. This type of bridge exists mainly on those that are specific to each blockchain (Harmony Bridge, Wrapped Bitcoin bridge, Avalanche Bridge, etc.);
- Decentralized bridges : these are based on a smart contract or an algorithm that eliminates the need to resort to an intermediary. Thus, users do not need to trust any entity using this type of bridge. Bridge-type security is thus linked to that of the underlying network. Also called trustless bridges (Wormhole by Solana, Cosmos IBC, Snow Bridge by Polkadot, etc.).
There are different types of connection allowed by the bridges:
- L1-L1 : connects two layer 1 blockchains together like Ethereum and Solana;
- L1-L2 : connects the main chain of a network with a layer 2 solution like Ethereum with Polygon;
- L2-L2 : connects two layer 2 solutions of the same blockchain, between them like Arbitrum and Optimism for the Ethereum network.
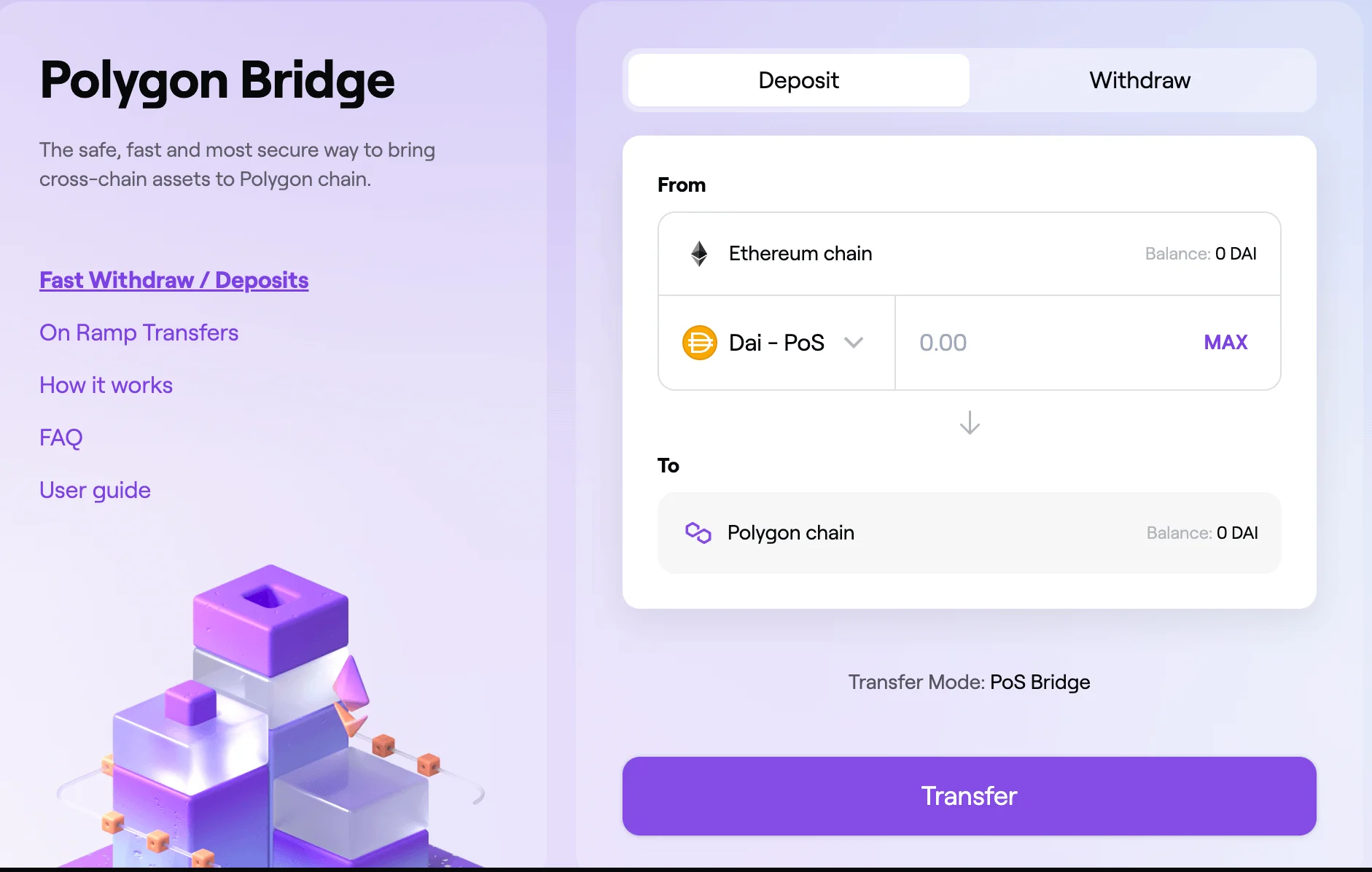
Figure 2: Overview of using the Polygon bridge (L1-L2 transfer)
We can imagine layer 1 blockchains as cities with L1-L1 bridges playing the role of highways linking cities together. The other types of bridges (L1-L2 and L2-L2) play the role of roads connecting the different points of interest of a city.
Bridges transfer assets from one chain to another in several ways:
- Lock and Mint : assets on the source blockchain are locked and an equivalent is mint on the destination blockchain. The most telling example is the Wrapped Bitcoin bridge which locks BTC on the Bitcoin blockchain and mints WBTC on Ethereum. It is also the most widely used bridge in the industry ;
- Burn and Mint : a bridge of this type burns the cryptocurrencies of the source blockchain and mints an equivalent on the destination blockchain;
- Atomic Swaps : these bridges exchange the cryptocurrencies of the source blockchain with the cryptocurrencies of the destination blockchain. This type of bridge relies on smart contracts that automatically execute these exchanges, which makes it possible to free oneself from the use of a third party as with the first two transfer methods.
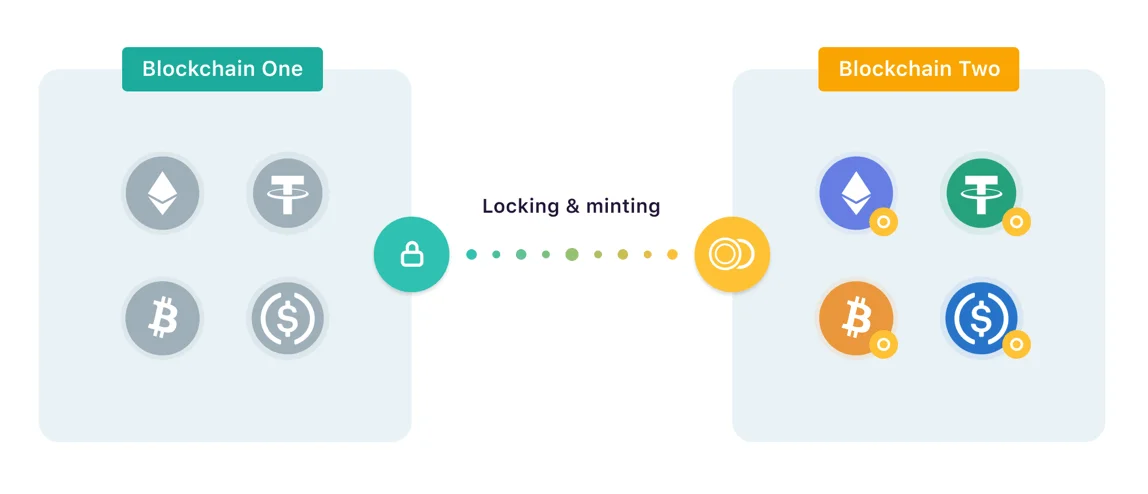
Figure 3: Illustration of a bridge using the Lock and Mint process
Take the Wormhole bridge as an example . To upgrade from an ETH to its equivalent on the Solana network, Wormhole locks the user’s ETH and mints the Wrapped Ethereum (WETH) token on Solana. During this process, the user therefore no longer sees the ETH on the Ethereum blockchain, which has been replaced by WETH on the Solana blockchain.
Another well-known example is the Lightning Network . Layer 2 of Bitcoin can also be used as a bridge since it is possible to create a payment channel there that uses different cryptocurrencies: we can send a payment in Bitcoin (BTC) and the recipient can receive the equivalent in Litecoin ( LTC) through an atomic swap.
How is a bridge useful?
Bridges make it possible to transfer information and cross-chain cryptocurrencies. At the level of protocol development, decentralized applications (dApps) can take advantage of the strengths of different blockchains thanks to bridges and thus improve their performance . While for the user, it is about having the choice and taking advantage of the advantages of each network .
Finally, the interoperability offered by bridges allows developers from different ecosystems to work together to build new, more efficient platforms.
Let’s see some real use cases to illustrate the importance of bridges in decentralized finance (DeFi). Let’s say we have Ether (ETH) on the Ethereum network, but we find the transaction fees a bit high to make a transfer.
By using a bridge connecting Ethereum to a second layer solution such as Optimistic Rollup or ZK Rollup , it is possible to benefit from lower transaction fees .
Another example on the Aave lending protocol. We lend USDC to it on the Ethereum network, but find that the interest rate is higher on the Avalanche blockchain.
We can thus use a bridge to transfer our USDC from the Ethereum network to Avalanche and thus benefit from a better interest rate .
Finally, and this is perhaps the most classic case, bridges allow users to explore the ecosystems of other blockchains without having to sell and buy another cryptocurrency . You can thus transfer your ETH to another layer 1 blockchain via a bridge to test the native applications of the latter while keeping your ETH.
Why are bridges so vulnerable?
You may not have missed it, but bridges have been the victims of many hacks in recent years.
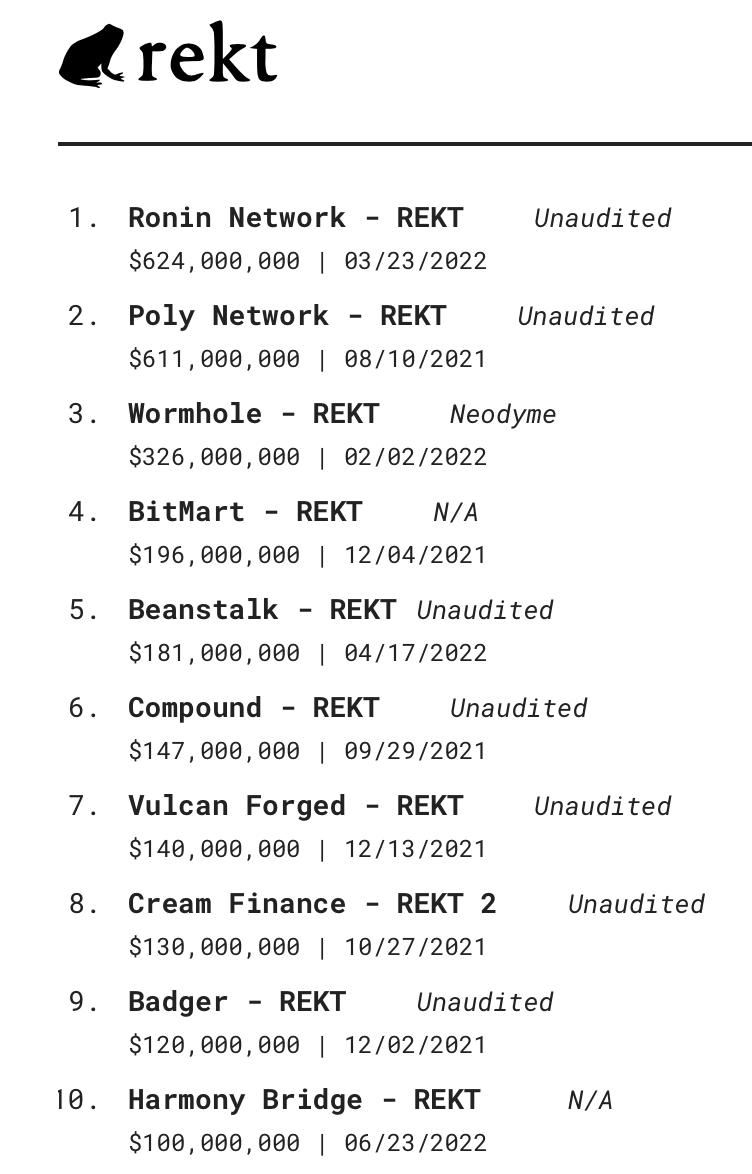
Figure 4: Overview of the biggest hacks in the cryptocurrency industry
To be more precise, the 3 biggest hacks in the industry concern bridges:
- Ronin Network (March 2022): $635 million stolen;
- Poly Network (August 2021): $611 million stolen;
- Wormhole (February 2022): $326 million stolen.
The Ronin bridge is a centralized bridge , while Wormhole and Poly Network are decentralized . The problem therefore does not necessarily come from the type of bridge, since each of them have their own faults .
For example, the Ronin bridge uses a multi-signature wallet for the custody of user-locked cryptocurrencies. When it was hacked, the Ronin bridge had 9 validators and 5 signatures (55.55%) were needed to approve deposits and withdrawals.
4 of these 9 signatures were held by the team at Sky Mavis , the company behind the Axie Infinity blockchain game, thereby creating a point of failure that hackers used. Thus, the latter managed to control the 4 signatures of Sky Mavis.
All they needed was a signature, which they were able to recover by taking control of Axie Infinity’s Decentralized Autonomous Organization (DAO).
Then all they had to do was steal users’ funds. Sky Mavis only realized the hack a week later, which also highlights the lack of effectiveness of the monitoring mechanisms of a centralized bridge.
Decentralized bridges are not left out since they can be exploited thanks to bugs or vulnerabilities in their code. The Wormhole hack is a good example. A bug located in the Wormhole smart contracts allowed a hacker to exploit the production process of WETH tokens and thus mint a lot of them (120,000) without locking real ETH beforehand.
A certain pessimism from industry players
Vitalik Buterin, the famous co-founder of Ethereum, is very pessimistic about the future of cross-chain applications .
According to him, bridges carry risks for the ecosystem . If we transfer 1,000 ETH to a bridge to receive 1,000 WETH to Solana, and the Ethereum blockchain suffers a 51% attack, then the attacker could deposit ETH into the bridge and rollback the transaction once the Solana blockchain confirmed it . Such manipulation would not be possible without bridge.
Thus, the Solana-WETH smart contract would no longer be balanced : there would be less ETH locked on Ethereum than WETH in circulation on Solana. Our WETH could be worth nothing depending on the amount stolen by the attacker. Vitalik adds on this subject:
“ It is always safer to hold native Ethereum assets on Ethereum or native Solana assets on Solana rather than owning native Ethereum assets on Solana and native Solana assets on Ethereum .”
He also points out that the more interdependent blockchains are, the higher the likelihood of systemic risk . If we are heading towards such a future, this risk will only increase.
It should be noted, however, that a 51% attack on the Ethereum blockchain is highly unlikely and this type of attack is more likely to happen on less robust and less used blockchains . Such a blockchain can thus jeopardize other more robust blockchains because of bridges.
Anyway, there are points on which we can rely to gauge the risks of bridges . The number of signatures as well as the ratio necessary for any withdrawal approval should be carefully considered for centralized bridges. Security audits and mechanisms preventing unusually large withdrawals should also be in place.
Our opinion on bridges
Bridges are an indispensable tool to link two ecosystems like Ethereum and Avalanche. They offer many possibilities, although this can come at the expense of security .
These are protocols that are, at the time of writing, more vulnerable than others for various reasons. This may change in the future as recent major hacks push developers to focus on the security of their creations .
Anyway, for the moment it is necessary to assess the risk of using a bridge and to act accordingly. This is why it is not highly recommended to transfer all of your native assets from one blockchain to another .
However, bridges are still great tools to take advantage of the advantages of each ecosystem and to navigate decentralized finance and the Web3, with the many blockchains and layer 2 solutions that exist, while alleviating the pressure on the Ethereum blockchain.
Thus, developers integrate bridges into their decentralized applications to make them multi-chain and take advantage of these advantages without having to choose a single and unique ecosystem, with the aim of building the Web3 of tomorrow.